Five NSA SPY Programs Everyone Should Know About
The Five NSA Programs You Should Know About
“Taken together, the revelations have brought to light a global surveillance system that cast off many of its historical restraints after the attacks of Sept. 11, 2001. Secret legal authorities empowered the NSA to sweep in the telephone, Internet and location records of whole populations.”
Barton Gellman in The Washington Post, December 23, 2013.
It’s been a little over a year since revelations from Edward Snowden’s historic NSA leak started appearing in newspapers around the world, and information about new surveillance programs is still surfacing every month. Last week, The Washington Post analyzed 160,000 NSA records and found that “ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted” by NSA surveillance programs. Four days later, Glenn Greenwald released the names of five distinguished Muslim-American men whose emails were being monitored by the NSA, none of whom are suspected of any wrongdoing.
Here’s a roundup of the five (previously) top-secret NSA surveillance programs that you should know about.
Here’s a roundup of the five (previously) top-secret NSA surveillance programs that you should know about.
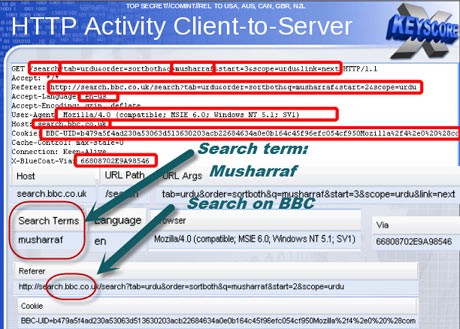
1. XKeyscore
Speaking from Hong Kong last June to journalist Glenn Greenwald and filmmaker Laura Poitras, former NSA contractor Edward Snowden made his most famous statement about the extent of NSA mass-surveillance programs: “I, sitting at my desk, had the authority to wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email.”
Journalists had already known about NSA efforts to collect internet and phone data for nearly a decade. By 2007, the NSA was adding one to two billion internet records to its databases daily. In 2010, The Washington Post reported that “every day, collection systems at the [NSA] intercept and store 1.7 billion emails, phone calls and other types of communications.” What we didn’t know was whose communications were being stored, and what ability NSA analysts had to access them.
When Snowden revealed the stunning power he had as a contractor for the NSA, he was referring to the NSA’s XKeyscore program — a program previously unknown to the public — which gives analysts the ability to easily search through the staggering amount of internet data collected and stored by the NSA every day.
Journalists had already known about NSA efforts to collect internet and phone data for nearly a decade. By 2007, the NSA was adding one to two billion internet records to its databases daily. In 2010, The Washington Post reported that “every day, collection systems at the [NSA] intercept and store 1.7 billion emails, phone calls and other types of communications.” What we didn’t know was whose communications were being stored, and what ability NSA analysts had to access them.
When Snowden revealed the stunning power he had as a contractor for the NSA, he was referring to the NSA’s XKeyscore program — a program previously unknown to the public — which gives analysts the ability to easily search through the staggering amount of internet data collected and stored by the NSA every day.
Using XKeyscore, an NSA analyst can simply type in an email address or IP address of a “target” and access their emails, search history, visited websites, and even Facebook chats. The program’s leaked slides boast that XKeyscore’s ability to analyze HTTP data allows it to see “nearly everything a typical user does on the Internet.”
“The NSA has trillions of telephone calls and emails in their databases that they’ve collected over the last several years. And what these programs are, are very simple screens, like the ones that supermarket clerks or shipping and receiving clerks use, where all an analyst has to do is enter an email address or an IP address, and it does two things. It searches that database and lets them listen to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you’ve entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future.”
Glenn Greenwald to ABC News’ George Stephanopoulos, July 27, 2013
Original Report: “XKeyscore: NSA tool collects ‘nearly everything a user does on the internet,’” The Guardian, July 31, 2013
2. FASCIA
FASCIA is the NSA’s real-life Marauder’s Map. In December 2013, Barton Gellman and Ashkan Soltani of The Washington Postreported that FASCIA was collecting nearly 5 billion pieces of location data from hundreds of millions of cellphones worldwide every day.
For your cell phone to work, your service provider needs to know its approximate location. Your phone transmits this information to the nearest cell towers, which the network can then use to triangulate your location. According to leaked NSA documents, FASCIA works by storing this location data when it is passed along the cables that connect different mobile networks. An NSA analyst sitting at a desk in Maryland can then search through this stored data to track the location of a specific phone user.
Perhaps the most interesting (and scariest) functionality of FASCIA is its “Co-Traveler Analytics.” By comparing a known target’s cell phone location with the location of other cell phones during an hour-long time window, the NSA can isolate groups of cell phones traveling together to find associates of the known target.
For your cell phone to work, your service provider needs to know its approximate location. Your phone transmits this information to the nearest cell towers, which the network can then use to triangulate your location. According to leaked NSA documents, FASCIA works by storing this location data when it is passed along the cables that connect different mobile networks. An NSA analyst sitting at a desk in Maryland can then search through this stored data to track the location of a specific phone user.
Perhaps the most interesting (and scariest) functionality of FASCIA is its “Co-Traveler Analytics.” By comparing a known target’s cell phone location with the location of other cell phones during an hour-long time window, the NSA can isolate groups of cell phones traveling together to find associates of the known target.
Original Report: “NSA tracking cellphone locations worldwide, Snowden documents show,” The Washington Post, December 4, 2013
3. Optic Nerve
Think TSA full-body scanners are intrusive? The UK’s surveillance agency GCHQ collaborated with the NSA to create Optic Nerve, a program that automatically stores webcam images of users chatting on Yahoo Messenger.
During one six-month period in 2008, Optic Nerve collected images from 1.8 million Yahoo accounts. It inserts each image, even those without a known target, into NSA databases, which can then be searched by analysts using XKeyscore. Again, all this happens without a court warrant.
Surprising to no one besides the NSA, an estimated 3.4%-10.8% of the images taken were sexually explicit:
Yahoo denied any knowledge of Optic Nerve, calling it “a whole new level of violation of our users’ privacy,” and promised to start to encrypt all Yahoo services by April 2014. As of today, Yahoo Messenger remains unencrypted.
Original Report: “Optic Nerve: millions of Yahoo webcam images intercepted by GCHQ,” The Guardian, February 27, 2014
Original Report: “Optic Nerve: millions of Yahoo webcam images intercepted by GCHQ,” The Guardian, February 27, 2014
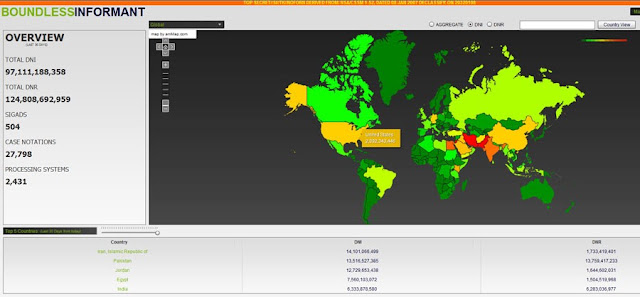
4. Boundless Informant
Boundless Informant, besides having a unenviably unsubtle name for NSA officials to have to explain front of Congress, is perhaps the most damning evidence so far that the NSA is conducting mass surveillance inside the United States.
Boundless Informant helps the NSA analyze and visualize the, well, boundless amounts of metadata information it collects around the world. (Metadata, or “data about data”, is all the information about a piece of data besides the actual content of the data. For example, metadata about telephone calls includes the phone numbers of the caller and recipient, as well as the location and duration of the call, but not the words in the call itself.)
Boundless Informant helps the NSA analyze and visualize the, well, boundless amounts of metadata information it collects around the world. (Metadata, or “data about data”, is all the information about a piece of data besides the actual content of the data. For example, metadata about telephone calls includes the phone numbers of the caller and recipient, as well as the location and duration of the call, but not the words in the call itself.)
The top surveilled countries in 2013 were Iran, Pakistan, Jordan, Egypt and India. Image from The Guardian.
The map above shows that in March 2013 alone, the NSA collected over 73 billion metadata records worldwide. Despite the NSA’s assurance that it does not intentionally collect data on Americans, nearly 3 billion pieces of metadata were collected from the United States alone.
If you want to see what your own metadata looks like, engineers at the MIT media lab developed a program called Immersion that analyzes your email metadata to create a cluster chart of your social connections.
Original Report: “Boundless Informant: the NSA’s secret tool to track global surveillance data,” The Guardian, June 11, 2013
If you want to see what your own metadata looks like, engineers at the MIT media lab developed a program called Immersion that analyzes your email metadata to create a cluster chart of your social connections.
Original Report: “Boundless Informant: the NSA’s secret tool to track global surveillance data,” The Guardian, June 11, 2013
5. Dishfire
Like FASCIA, Dishfire targets cell phones. More specifically, it collects nearly 200 million text messages daily around the world, using them to view financial transactions, monitor border crossings, and meetings between unsavory characters.
According to The Guardian, each day the NSA stores:
According to The Guardian, each day the NSA stores:
• More than 5 million missed-call alerts, for use in contact-chaining analysis (working out someone’s social network from who they contact and when)
• Details of 1.6 million border crossings a day, from network roaming alerts
• More than 110,000 names, from electronic business cards, which also included the ability to extract and save images.
• Over 800,000 financial transactions, either through text-to-text payments or linking credit cards to phone users
Using Dishfire, the NSA can extract names, geocoordinates, missed calls, SIM card changes, roaming information, travel, financial transactions, and passwords from a user’s cell phone.
According to The Guardian, the NSA “has made extensive use of its vast text message database to extract information on people’s travel plans, contact books, financial transactions and more — including of individuals under no suspicion of illegal activity.”
The NSA has stated that they removes all text messages involving U.S. citizens from their databases, and that “privacy protections for U.S. persons exist across the entire process concerning the use, handling, retention, and dissemination of SMS data in Dishfire.” Based on this week’s Washington Post report that nearly half of NSA surveillance files involve Americans, it’s hard to take their word for it.
Original Report: “NSA collects millions of text messages daily in ‘untargeted’ global sweep,” The Washington Post, January 16, 2014








Comments
Post a Comment