Names and definitions of leaked CIA hacking tools
Names and definitions of leaked CIA hacking tools

The WikiLeaks-hosted “Vault7” collection of documents allegedly leaked from within the CIA’s Computer Operations Group is a messy mix of jargon, incomplete info and broken (or redacted) links. The information is interesting, but it’s quite difficult to find a basic description of many of the terms used, even using the search function. So for everybody’s convenience I’ve gone through the whole pile of docs and listed as many of the tools and techniques mentioned by spook IT as I could find.
If there’s any indication of what the thing does, I’ve included it, though some of these are just educated guesses based on the devices being tested on, comments from their developers and so on. All data (such as OS versions affected) is as of the latest document I could find in the leaked files. Images are all from the leaks, as well.
I’ve included tools that seemed significant but had no real information on them at the bottom of each list. I did not include links because projects and their descriptions are often spread across multiple pages or PDFs. I also did not include commercial tools (such as Lockheed Martin’s DART software testing suite) or operation names (like JQJHAIRPIECE) that seem to merely be specific deployments of other tools.
This list is by no means comprehensive or authoritative, nor should the leaked files be considered comprehensive of the hacking tools created and used by the CIA. I’ll be updating it as I find more or things are un-redacted.
Embedded Development Branch (EDB)
This branch is concerned with compromising and embedding implants in purpose-built devices like VoIP phones, workstations and smart devices like TVs. They do both hardware and software design.
- Pterodactyl – A “custom hardware solution to support media copying”; it uses small single-board computers like Raspberry Pi to copy data from an asset computer
- SparrowHawk – Keylogger intended for use across multiple architectures and Unix-based platforms
- DerStarke – Boot-level rootkit implant for Apple computers
- GyrFalcon – Tracks the client of an OpenSSH connection and collects password, username and connection data
- SnowyOwl – Uses OpenSSH session to inject code to target asset
- HarpyEagle – Hardware-specific tool to gain root access to Apple’s Airport Extreme and Time Capsule
- BaldEagle – An exploit for Unix systems’ Hardware Abstraction Layer
- MaddeningWhispers – Remote access to devices compromised with the Vanguard exploit
- CRUCIBLE – An “automated exploit identification” tool
- YarnBall – Covert USB storage for deployment of payloads and storage of exfiltrated data
- GreenPacket – Router implant kit
- QuarkMatter – Another boot-level rootkit implant for Apple computers
- Weeping Angel – Smart TV implant kit (we wrote about it separately)
- Hive – Basic implant suite for Windows and Unix setups aimed at “providing an initial foothold for the deployment of other full featured tools”
- Honeycomb – Server for data coming from Swindle or Blot proxy servers
- CutThroat – Virtual machine system apparently for hosting proxy servers to send asset data to
- Bee Sting – iFrame injection technique for HTTP connections
- Sontaran – An attempt to compromise the Siemens OpenStage VoIP phone
- Secret Squirrel (SQRL) – ???
Remote Development Branch
There isn’t much data on RDB; the only tool listed is for getting at secure databases, so that’s a hint.
- Umbrage – This team, among other things, seems to have collected hacker tools and techniques in use around the web, and also sorted through the Hacking Team leak for useful code and documentation — helpful for development or attribution of hacks
- ShoulderSurfer – Tool used to extract data from Microsoft Exchange databases
Operational Support Branch
In addition to maintaining some useful all-purpose utilities, OSB creates custom solutions for individual operations or assets, with a focus on compromising Windows machines and apps.
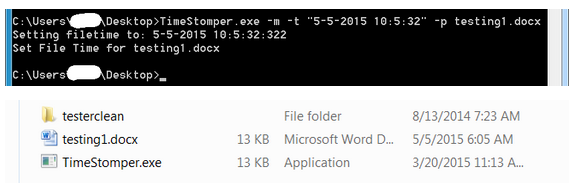
- Time Stomper – Used to modify timestamps on files so that they match what an operation or asset requires
- Munge Payload – Tool for encrypting payloads and/or modifying them to avoid detection
- Magical Mutt – Appears to be a malware-style DLL injector and process monitor
- Flash Bang – Hijack that breaks out of the Internet Explorer sandboxed process and then escalates privileges on the target machine
- RickyBobby – Basic Windows implant comprising DLLs and scripts that sends its info to listening post server app Cal — yes, they’re Talladega Nights references
- Fight Club – Set of infected VLC, WinRAR, TrueCrypt, Shamela and Microsoft Office Standalone installers that deployed RickyBobby instances, for placement on thumbdrives used in an operation
- Melomy DriveIn – Hijack of a VLC DLL that launches a RickyBobby instance — unclear if it’s the one in Fight Club
- Rain Maker – Compromised portable VLC player that covertly collects files from an air-gapped computer when launched from a user’s USB drive
- Improvise – Set of interoperable tools used to collect and exfiltrate data from a Windows, Mac or Linux machine — with bar-themed names (Margarita, Dancefloor, Jukebox) corresponding to the OS
- Basic Bit – Keylogger for Windows machines
- Fine Dining – Not software exactly but apparently a menu that operatives can order from to get a custom tool for an operation — a fake PDF that launches on a Mac and scours the drive for all audio files, for instance
- HammerDrill – CD/DVD monitoring tool that also allows files to be compromised as they’re being written to a disc
- Taxman – ???
- HyenasHurdle – ???
Automated Implant Branch
AIB seems to concern itself with self-running implants. Many of these are not documented or described, but have file lists that reveal a little about their purpose.
- Frog Prince – Fully integrated implant system inclusive of command and control, listening post and implant software
- Grasshopper – Highly configurable tool used to place various implants on Windows machines (Cricket is a relative)
- Caterpillar – Tool for preparing files acquired from a system for secure transport
- AntHill – Appears to be a file management component for installed implants
- The Gibson – Appears to be a component of command and control servers and listening posts.
- Galleon – Set of nautically themed scripts and tools for securely copying files to a target computer
- Assassin – ???
- HercBeetle – ???
- CandyMountain – ???
- Hornet – ???
- Cascade – ???
- MagicVikings – ???
Network Devices Branch
This branch is all about routers and switches, from industrial-level gear to home devices, all of which require device or class-specific exploits and kits. The leaks largely consist of highly technical test results and developer instructions that only hint at the software’s capabilities.
- Cannoli – Implant for Linksys devices
- WAG200G – Implant installer for Linksys routers that works alongside Cannoli
- Slasher – Appears to be a port monitor
- Cinnamon – Implant for Cisco routers
- Earl Grey – Another implant possibly for Cisco routers
- Aquaman – Implant for Linux-based systems, possibly routers (HGs or home gateways) in particular
- Bumble – Implant for HP routers
- Perseus – Appears to be an implant for routers using PowerPC architecture
- Panda Poke – A “credless” exploit (i.e. requires no login credentials) for Huawei router devices
- Panda Flight – Covert tunneling tool for Huawei devices
- Panda Sneeze – Unclear purpose but part of the Panda suite along with PandaMitt, PandaScore and others
- ChimayRed – Exploit used against MikroTik routers running RouterOS that allows payloads to be installed on the device
- Felix – Appears to be a listening post for MikroTik routers
- HG – Possibly HunGrrr, general-purpose tool for accessing remote networking devices; used as a component or step in many tests and projects
- BuzFuz – ???
- Cytolysis – ???
- Powerman – ???
Non-branch-specific Projects
These aren’t listed under any specific branch, though some refer to being under the jurisdiction of one or another, or based on a project out of EDB, NDB, etc.
- AfterMidnight – Seems to be a Windows privilege escalation scheme that uses one DLL to gain access for another (a “Gremlin”)
- Packrat – Tool for creating and automating listening posts with open-source and commercial software
- RoidRage – Implant/exploit for Android devices up to 5.X
- The.Net – Network configuration tool that imitates real-world internet and intranet conditions in a set of fictional corporations (Umbrella, Abstergo, etc.)
- Philosoraptor – Unclear, but “stated goal” is to demonstrate the business value of new tool suites and automated testing using a legitimate operational software product
- Marble Framework – Obfuscation tool that modifies source files so they can’t be traced to developers or teams
- Kraken – Appears to be an organizational tool for task management and project tracking
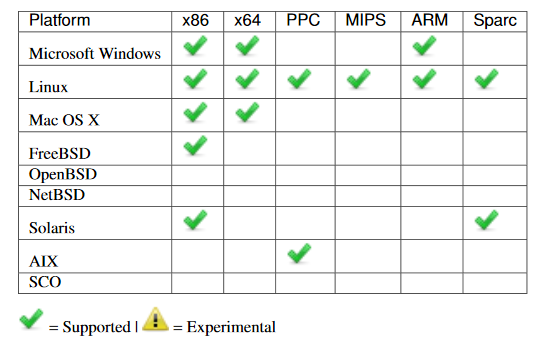
- Fluxwire – Contractor-provided distributed/mesh network tool (with extensive documentation) used to organize connected assets, supporting 9 OSes and 6 architectures
- Cocoon – ???
- Tremor – ???
iOS-specific
Some tools seem to be only mobile-specific, but these are largely aimed at iOS devices.
- Adderall – Tool to pull files and kernel cache from iOS devices
- ElderPiggy – Privilege escalation tool
- NightVision – Reads and records device’s kernel memory
- Nightskies – iOS implant, installed via CrunchyLimeSkies
- Mcnugget – Mission control utility for iOS implants
- HAMR – Framework for “throwing” browser exploits
- DRBOOM – Single-step implant installer for iOS up to 8.2
Android-specific
A number of exploits are referred to but redacted, so they’re not listed here.
- AngerQuake (renamed AngerManagement) – Collection of HAMR-related plug-ins for remote exploitation of Android devices
- Orion – Remote exploit for Android devices
- Freedroid – Privilege escalation tool



Comments
Post a Comment